Some things to know before you read this
* I have included an example source file, but don't download it expecting to have a free FUD crypter
* This guide doesn't cover every method of file undetection. I'm simply showing you one way you can decrease the number of detections your file gets.
* I'm not responsible for whatever shenanigans you pull with this information
What do anti-viruses look for in a file?
First off, you will need some basic understanding of how anti-viruses work. Exe files are simply lines of instruction, and each line is called an offset.
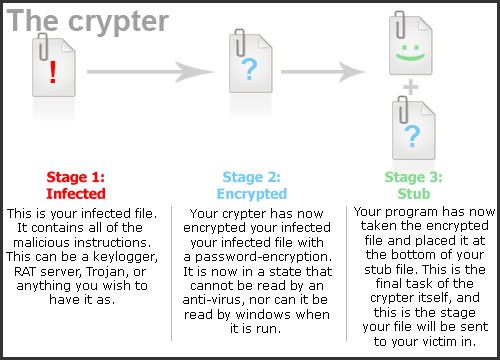
Your crypter is going to take the contents of an infected file, encrypt them, and place it at the bottom of a seemingly virus-free file called your "stub".
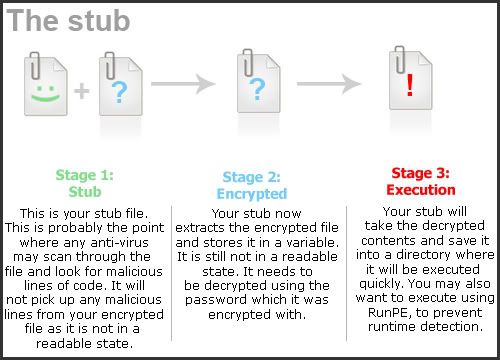
Your stub file will then extract the encrypted data from itself, decrypt it, then extract and run it.
This may sound like a complicated and confusing process, but it isn't. Here are some diagrams I made to show your what I mean:
I've created an example program. I have not tested how FUD it will actually make a file, but I can guarantee it is not anywhere near 100%. The reason I did this is because I want YOU to make your crypters. If you think you are completely lost at this point, perhaps you are not ready yet. Read some VB6 tutorials, look at example programs, and learn! When you think you are ready, read through this whole thing again.
I've thoroughly commented the code to help you
http://www.mediafire.com/download.php?zncawy1ztzm
Other things you can do
What will be detected now is completely dependent on your stub.
Some things you can do to make your stub further undetected:
- Do NOT take code from other programs!
- Change your variable or function names around to random things. (ex. dim stubFile as string can become dim hdfKd9jsd as string)
- Do not include the word "stub" anywhere in your application.
- After you've built your stub, go through it with a hex editor and try to find the word "stub" and take it out. Sometimes it ends up in there without you meaning to put it there.
- Remove the version information from your stub. I recommend Resource Hacker for doing this.
- When calling API's, use a function called CallApiByName. If you search around, I'm sure you will find an example of it.
- There are many other things you can do. Look around on Hack Forums or Hack Hound. There are lots of great discussions about undetection techniques.
- When test-scanning your file, use novirusthanks.org and check off "do not distribute." If you scan it with virustotal, they will distribute your file among the AV's.
- Try not to publicly distribute your crypter
- Don't give up!




2 comments:
very good tutorial
I've used Kaspersky security for many years, I'd recommend this product to everyone.
Post a Comment